The thirteen-month-old had mastered the word “dada” by the time I met her. Her parents were teaching her to communicate other concepts through sign language. Picture her, dark-haired and bibbed, in a high chair. Banana and mango slices litter the tray in front of her. More fruit litters the floor in front of the tray. The baby lifts her arms and flaps her hands.
Dada looks up from scrubbing the floor.
“Look,” he calls to Mummy, “she’s using sign language! All done.” He performs the gesture that his daughter seems to have aped: He raises his hands and rotates his forearms about his ulnas, axes perpendicular to the floor. “All done!”
The baby looks down, seizes another morsel, and stuffs it into her mouth.
“Never mind,” Dada amends. “You’re not done, are you?”
His daughter had a sign(-language) problem.

So does Dada, MIT professor Aram Harrow. Aram studies quantum information theory. His interests range from complexity to matrices, from resource theories to entropies. He’s blogged for The Quantum Pontiff, and he studies—including with IQIM postdoc Elizabeth Crosson—the quantum sign problem.
Imagine calculating properties of a chunk of fermionic quantum matter. The chunk consists of sites, each inhabited by one particle or by none. Translate as “no site can house more than one particle” the jargon “the particles are fermions.”
The chunk can have certain amounts of energy. Each amount corresponds to some particle configuration indexed by
: If the system has some amount
of energy, particles occupy certain sites and might not occupy others. If the system has a different amount
of energy, particles occupy different sites. A Hamiltonian, a mathematical object denoted by
encodes the energies
and the configurations. We represent
with a matrix, a square grid of numbers.
Suppose that the chunk has a temperature . We could calculate the system’s heat capacity, the energy required to raise the chunk’s temperature by one Kelvin. We could calculate the free energy, how much work the chunk could perform in powering a motor or lifting a weight. To calculate those properties, we calculate the system’s partition function,
.
How? We would list the configurations . With each configuration, we would associate the weight
. We would sum the weights:
.
Easier—like feeding a 13-month-old—said than done. Let denote the number of qubits in the chunk. If
is large, the number of configurations is gigantic. Our computers can’t process so many configurations. This inability underlies quantum computing’s promise of speeding up certain calculations.
We don’t have quantum computers, and we can’t calculate . Can we approximate
?
Yes, if “lacks the sign problem.” The math that models our system models also a classical system. If our system has
dimensions, the classical system has
dimensions. Suppose, for example, that our sites form a line. The classical system forms a square.
We replace the weights with different weights—numbers formed from a matrix that represents
. If
lacks the sign problem, the new weights are nonnegative and behave like probabilities. Many mathematical tools suit probabilities. Aram and Elizabeth apply such tools to
, here and here, as do many other researchers.
We call Hamiltonians that lack the sign problem “stoquastic,” which I think fanquastic.1 Stay tuned for a blog post about stoquasticity by Elizabeth.
What if has the sign problem? The new weights can assume negative and nonreal values. The weights behave unlike probabilities; we can’t apply those tools. We find ourselves knee-deep in banana and mango chunks.

Solutions to the sign problem remain elusive. Theorists keep trying to mitigate the problem, though. Aram, Elizabeth, and others are improving calculations of properties of sign-problem-free systems. One scientist-in-the-making has achieved a breakthrough: Aram’s daughter now rotates her hands upon finishing meals and when she wants to leave her car seat or stroller.
One sign problem down; one to go.

With gratitude to Aram’s family for its hospitality and to Elizabeth Crosson for sharing her expertise.
1For experts: A local Hamiltonian is stoquastic relative to the computational basis if each local term is represented, relative to the computational basis, by a matrix whose off-diagonal entries are real and nonpositive.

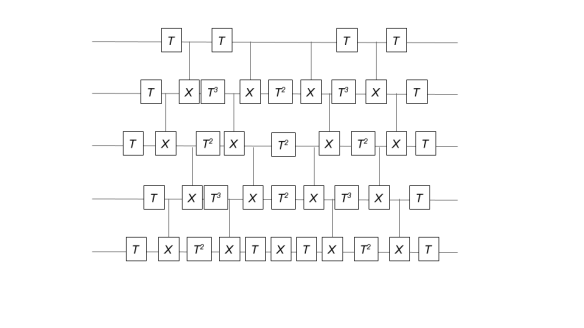
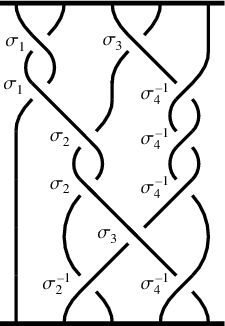 . Unfortunately, any obfuscation by compiling scheme has the problem that whoever understands the compiler well enough will be able to actually read the .out file (or notice a pattern in braids reduced to a compact “normal” form), and guess your number without resorting to a quantum computer. Surprisingly, even though Alagic et al.’s scheme doesn’t claim any protection under this attack, it still satisfies one of the theoretical definitions of obfuscation: if two people write two different sets of instructions to perform the same operation, and then each obfuscate their own set of instructions by a restricted set of tricks, then it should be impossible to tell from the end result which program was obtained by whom.
. Unfortunately, any obfuscation by compiling scheme has the problem that whoever understands the compiler well enough will be able to actually read the .out file (or notice a pattern in braids reduced to a compact “normal” form), and guess your number without resorting to a quantum computer. Surprisingly, even though Alagic et al.’s scheme doesn’t claim any protection under this attack, it still satisfies one of the theoretical definitions of obfuscation: if two people write two different sets of instructions to perform the same operation, and then each obfuscate their own set of instructions by a restricted set of tricks, then it should be impossible to tell from the end result which program was obtained by whom.